
This year's National Cybersecurity Awareness Month is coming to an end, but it does not mean that individuals, teams, organizations, and companies should stop caring about cybersecurity. As more and more of our lives is put online, the more our lives can be impacted by those seeking us harm on the Web. To wrap-up NCSAM 2019, we will be covering how to be safe when shopping online with E-Commerce.
E-Skimming
The Internet touches almost all aspects of our daily lives. We are able to shop, bank, connect with family and friends, and handle our medical records all online. These activities require you to provide personally identifiable information (PII) such as your name, date of birth, account numbers, passwords, and location information. #BeCyberSmart when sharing personal information online to reduce the risk of becoming a cyber crimes victim.
What Is E-Skimming?
Cyber criminals introduce skimming code on e-commerce payment card processing web pages to capture credit card and personally identifiable information and send the stolen data to a domain under their control.
How Does It Work?
A skimming code is introduced to payment card processing websites by:
- Exploiting a vulnerability in the website’s e-commerce platform
- Gaining access to the victim’s network through a phishing email or brute force of administrative credentials
- Compromising third-party entities and supply chains by hiding skimming code in the JavaScript loaded by the third-party service onto the victim website
- Cross site scripting which redirects customers to a malicious domain where malicious JavaScript code captures their information from the checkout page
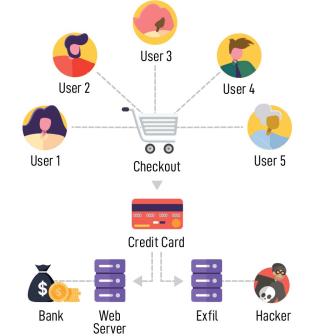
The malicious code captures credit card data as the end user enters it in real time. The information is then sent to an Internet-connected server using a domain name controlled by the actor. Subsequently, the collected credit card information is either sold or used to make fraudulent purchases.
Who Is Being Targeted?
Any business accepting online payments on their website is at risk of an e-Skimming attack. This threat has impacted e-commerce companies in the retail, entertainment, and travel industries as well as utility companies and third-party vendors. E-Skimming is also commonly targeting third-party vendors such as those who provide online advertisements and web analytics. The cyber criminals are evolving their tactics and have also been seen using malicious code that targets user and administrative credentials in addition to customer payment information.
What Are The Warning Signs?
- Complaints of fraudulent activity on several customers’ accounts after making a purchase from victim company.
- Identifying a new domain not known to be registered by victim company.
- JavaScript code has been edited.
How Can You Minimize the Risk?
The FBI recommends taking precautionary measures to mitigate the threat of e-Skimming attacks. In an attempt to make attribution, the FBI determined the malicious skimmer code has varied in complexity, which limits the ability to identify a specific set of indicators of compromise. Vulnerable companies should secure websites to prevent malicious code injection. In addition, companies should implement proper network segmentation and segregation to limit network exposure and minimize lateral movement of cyber criminals.
- Perform regular updates to payment software.
- Install patches from payment platform vendors.
- Implement code integrity checks.
- Keep anti-virus software updated.
- Ensure you are PCI DSS compliant.
- Monitor and analyze web logs.
- Refer to your Incident Response Plan, if applicable.
What Can You Do If You Are A Victim?
- Identify source of skimming code to determine access point - network, third party, or other.
- Save a copy of skimming script or malicious loader domain to report to law enforcement.
- Change pertinent credentials.
- Refer to your Incident Response Plan, if applicable.
- File a detailed complaint at www.IC3.gov and review additional resources under the “Press Room” link.
Weekly Tips
Return to October National Cybersecurity Awareness Month
Follow along each week of October as we give tips to help keep your online life safe and secure. Share your appreciation for NCSAM with #BeCyberSmart and #CyberAware.
Week 1 Week 2 Week 3 Week 4 Week 5

